This is a quick post based on a tweet shared by @g0njxa. Here we will build a Censys query to identify servers related to an IP related to PrivateLoader.
Initial Search
We can begin with an initial search on the IP Address using ip:185.198.57[.]117 .
This shows that the ip address is running two services on port 22 (SSH) and 80 (HTTP).
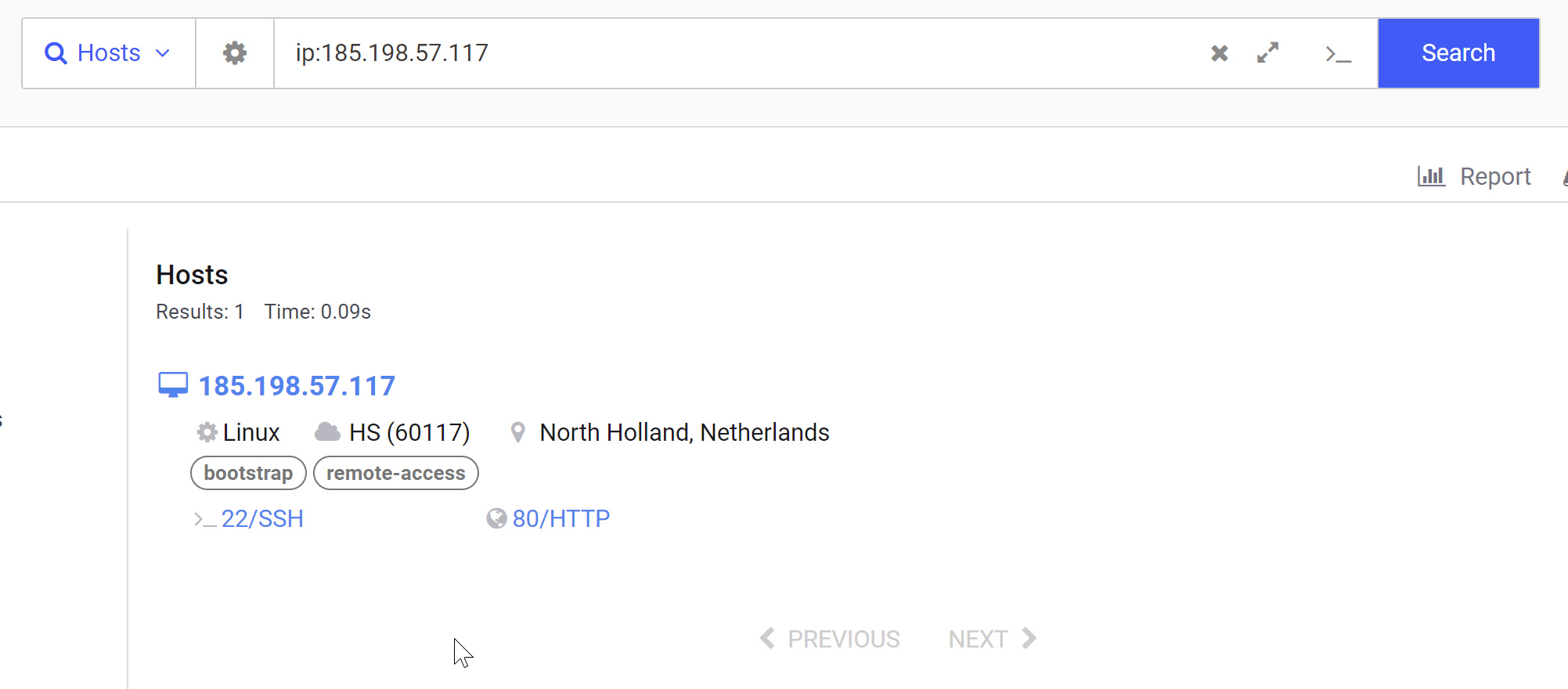
Investigating the address further, we can see a standard looking setup on SSH and a simple Apache server on port 80.
Within the HTTP Service, there is a relatively long HTTP Title containing Apache HTTP Server Test Page powered by CentOS.
There is also a very long response body which appears to be a default Apache page. I made the assumption that the Title and Body are both defaults and hence it doesn't really matter which one is used as a pivot.
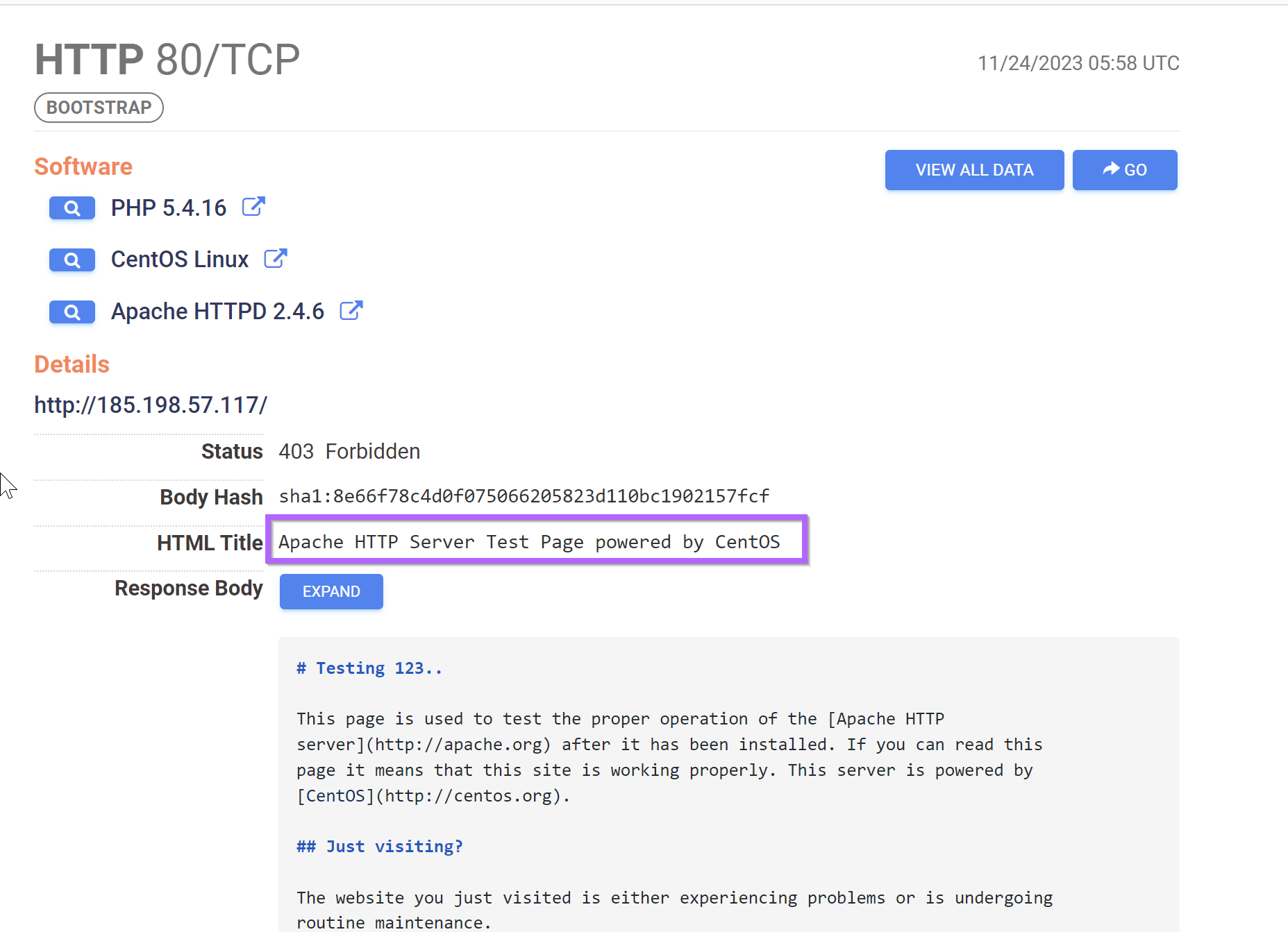
Now so far everything looks "default" and not easily signatured, but we can still go ahead and attempt a pivot on the HTML Title.
services.http.response.html_title="Apache HTTP Server Test Page powered by CentOS"
This returns ~332,310 results. Which is way too many for the HTML Title to be used on it's own.
Refining The Query By Limiting Service Count
If we recall from the initial search on the ip, there are only two running services (SSH and HTTP).
We can use this information to limit the search to servers with only 2 running services.
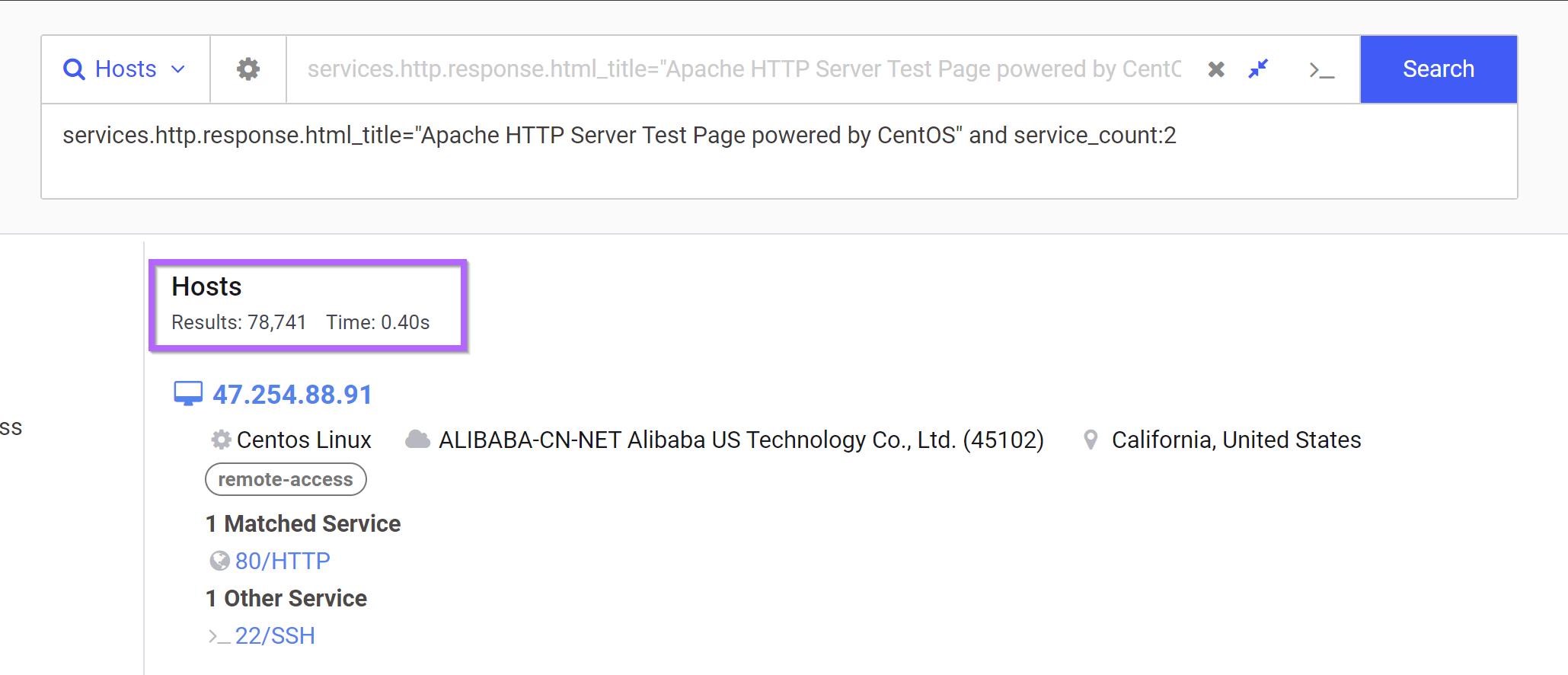
services.http.response.html_title="Apache HTTP Server Test Page powered by CentOS" and service_count:2
This reduces the results down to 78,741. Not great but much better than before.
Refining Results by Providing Specific Ports
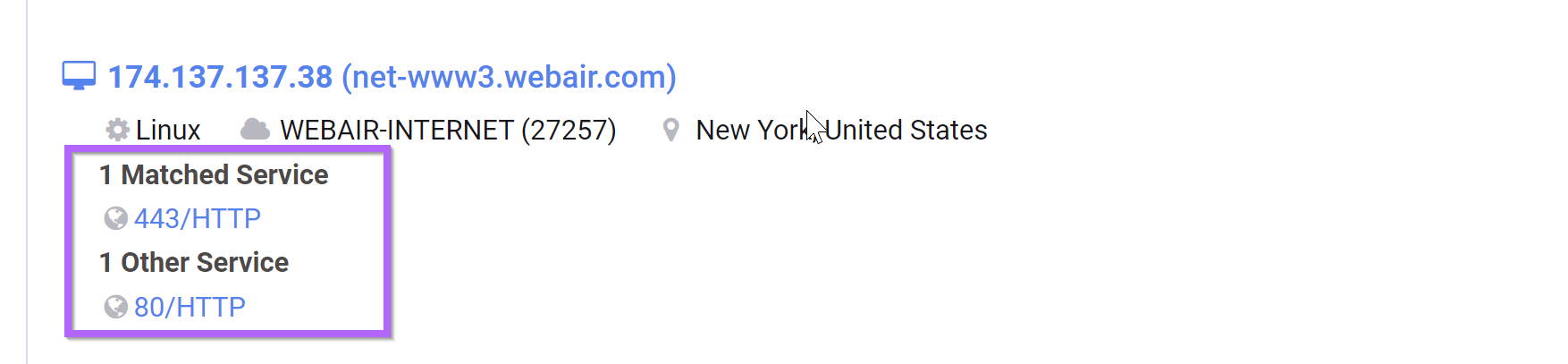
If we look at the second result from our previous search, we can see that it is running two services.
One on port 80, and one on port 443.
We can go ahead and remove these by specifying that we only want servers with port 22 and 80.
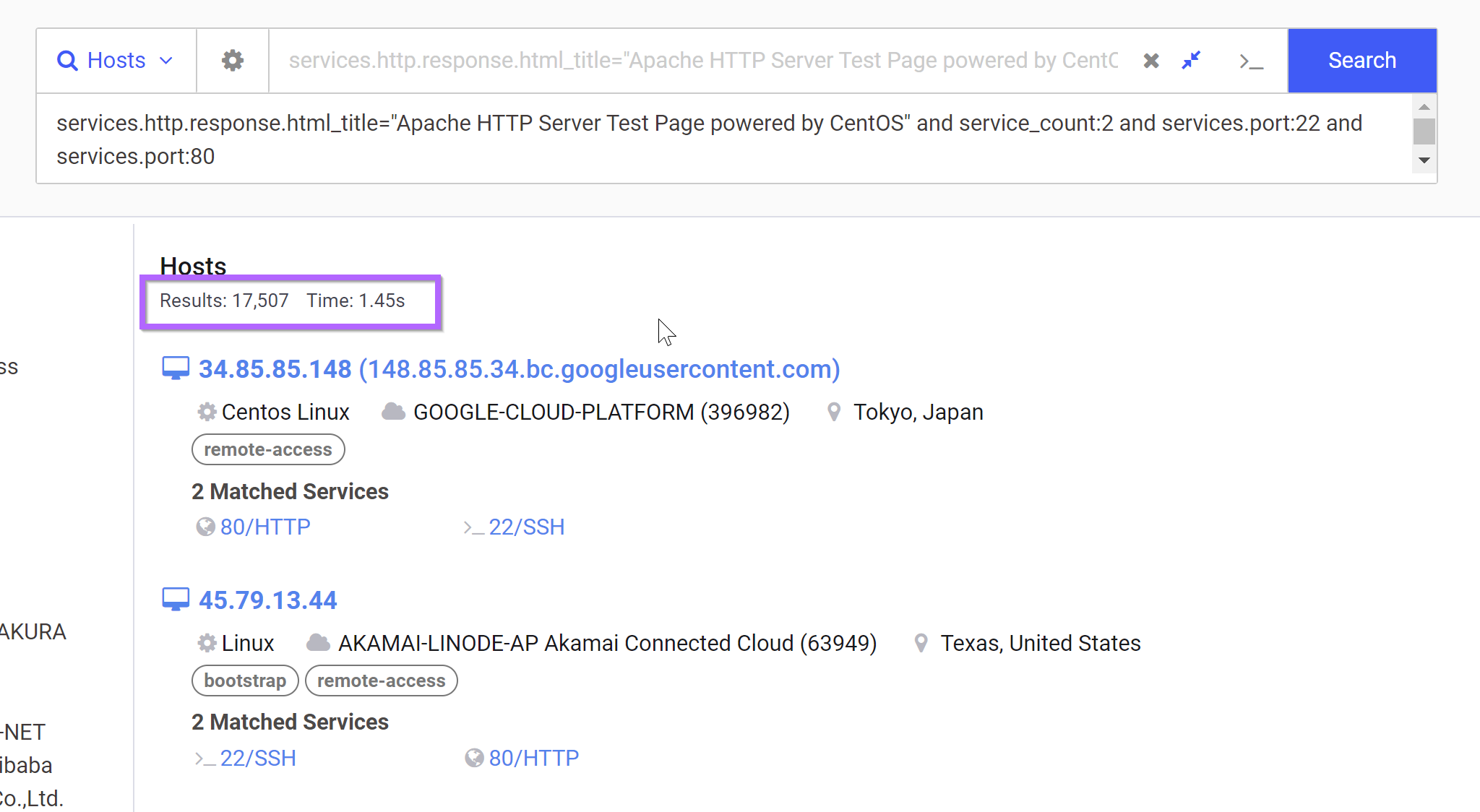
We can refine our search with the query below, which cuts down the results to ~17000
services.http.response.html_title="Apache HTTP Server Test Page powered by CentOS" and service_count:2 and services.port:22 and services.port:80
Now at this point I wasn't able to find any other useful pivot points within the HTTP or SSH services.
We can go ahead and pivot using the Autonomous System Number (ASN). This limits the results to servers/ips within a similar geographic location (or at least hosted by a similar hosting provider).
In my experience, the ASN should be used as a last resort when no other pivot points can be found. If an actor has set up their infrastructure well, then there will be servers across multiple ASN's and geographic locations. Limiting to a single ASN will miss servers in a separate location, but it's very useful when there aren't other options.
We can see the ASN number in the summary for the initial IP address.
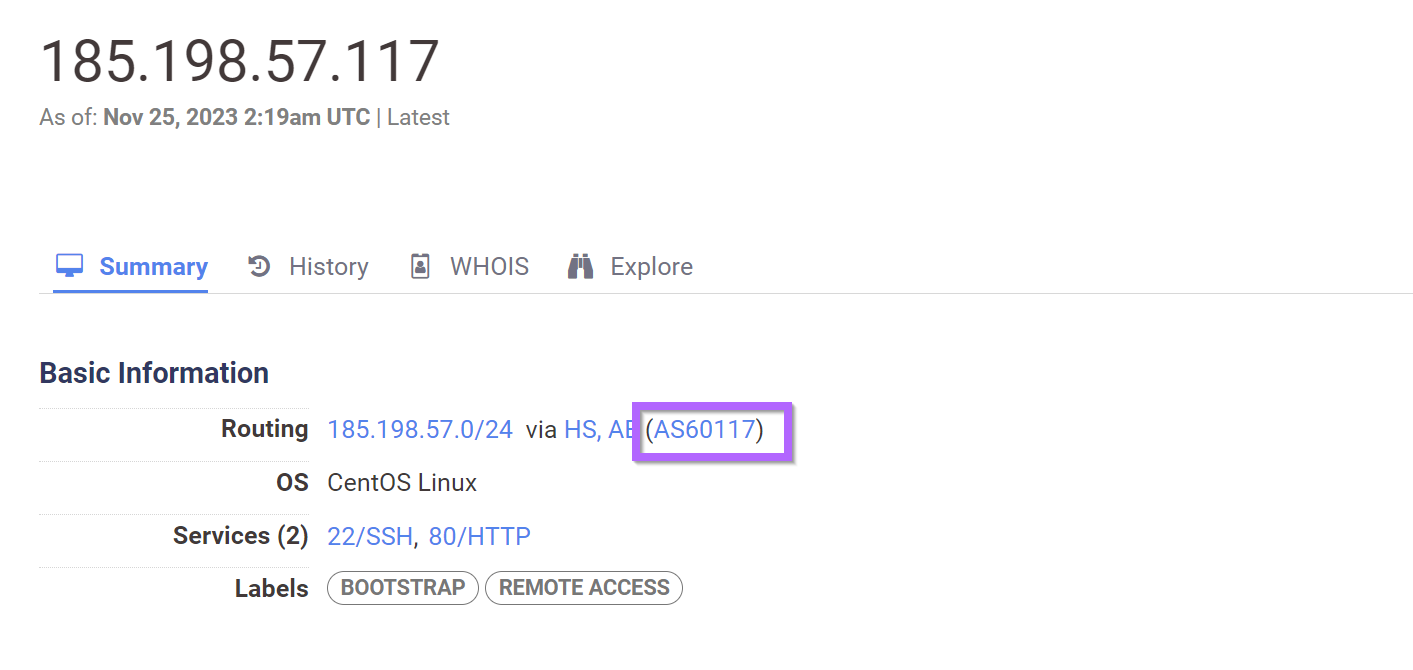
Now with the ASN Number added, we are down to only 12 results. A number as small as 12 is a good indicator that the results are all related.
services.http.response.html_title="Apache HTTP Server Test Page powered by CentOS" and service_count:2 and services.port:22 and services.port:80 and autonomous_system.asn="60117"
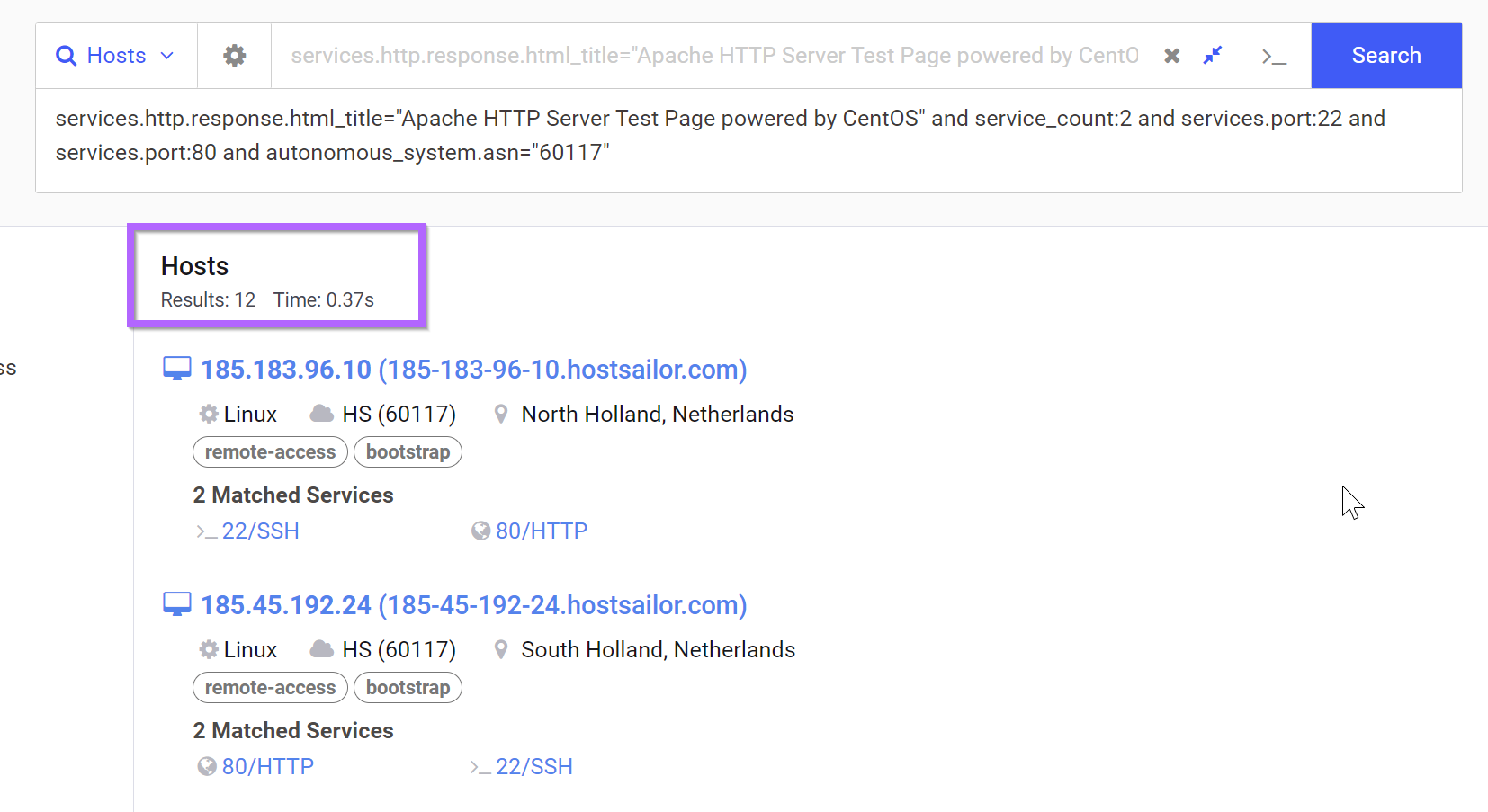
Investigating Results
Now at this point, all of the servers look the same (simple and default services), so it's difficult to determine if they are malicious using only Censys.
So we can go ahead and export a list and compare it to a reputation service like VirusTotal.
There are likely much better services out there than Virustotal, but VT is the standard and the most accessible so it's what we will use here
We can start by exporting an easy list of results from our search. This can be done with the "report" feature of Censys.
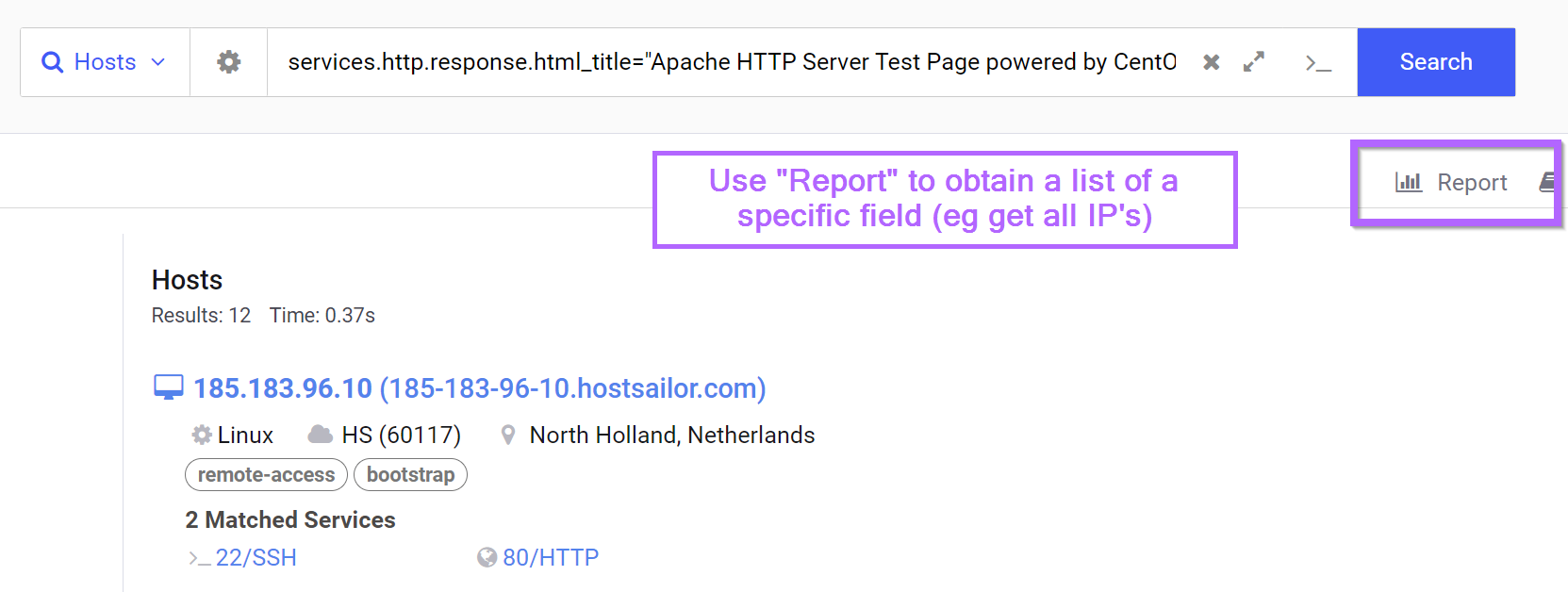
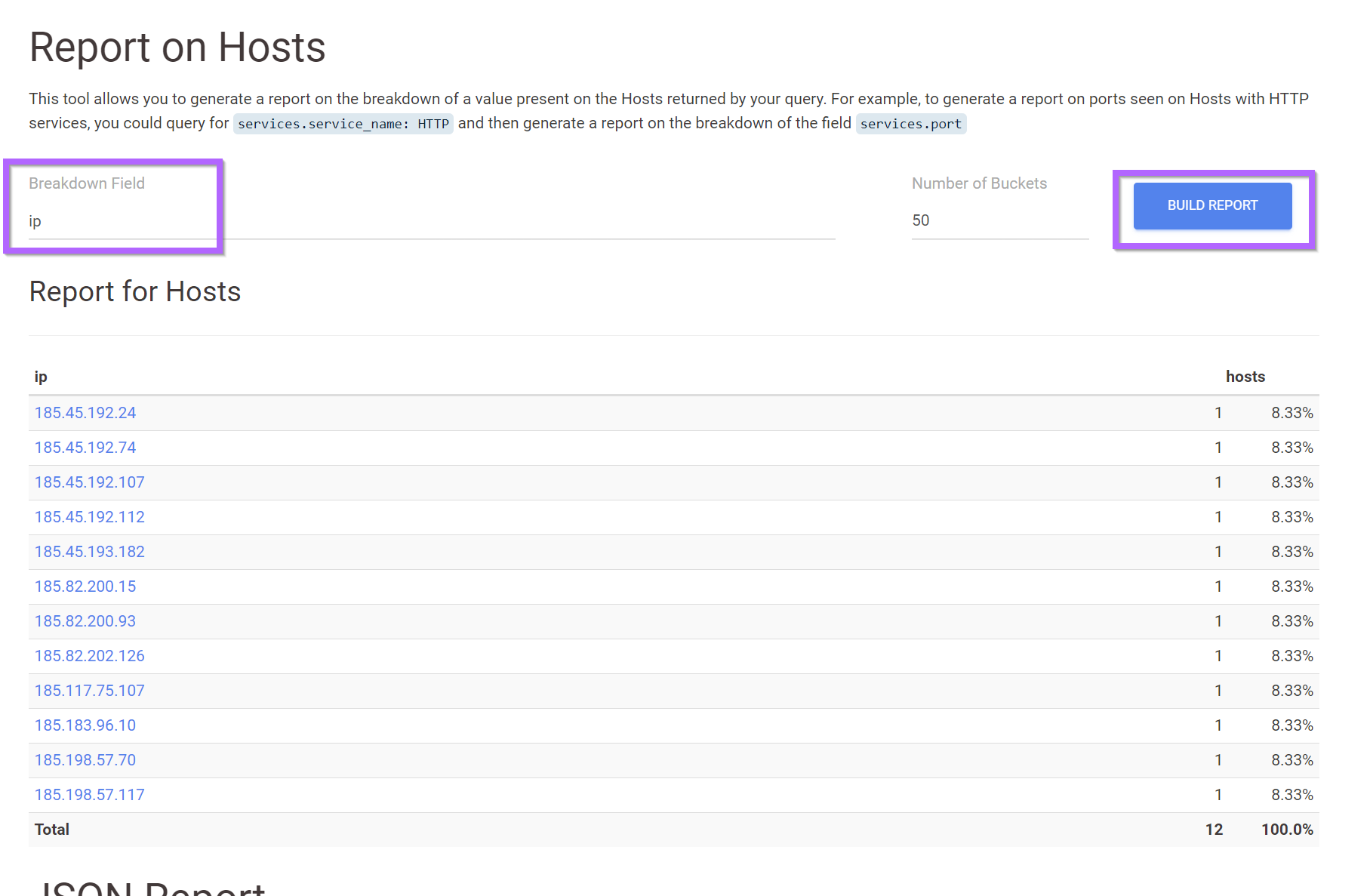
From the report function, we can specify the ip field and go ahead and build a report. (We can leave the "Number of Buckets" at 50, since our search returned less than 50 results)
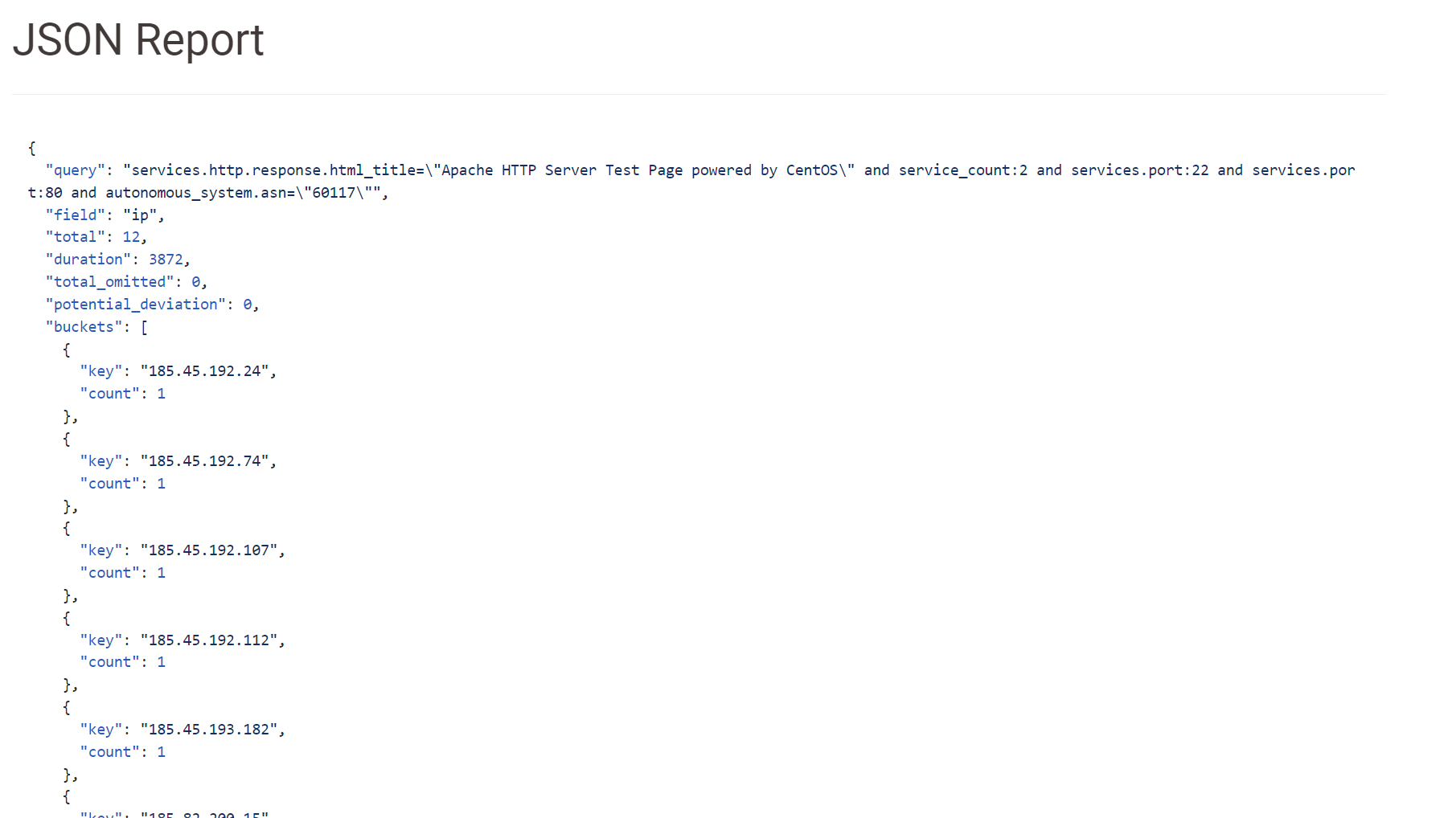
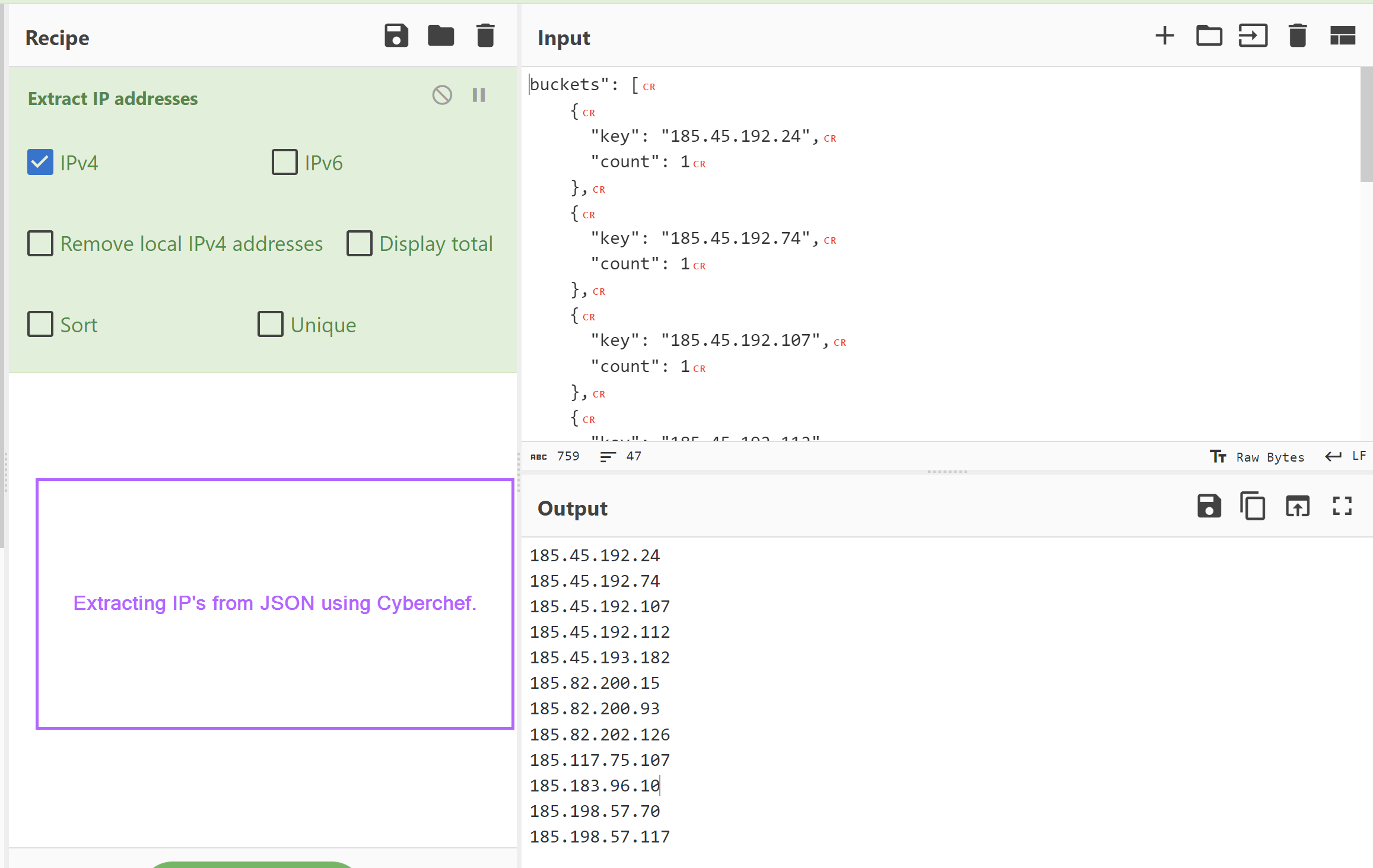
By scrolling down we can obtain the list in JSON format.
From here we can use CyberChef and Extract IP Addresses to get an easy list without needing to deal with JSON.
Checking Results in Virustotal
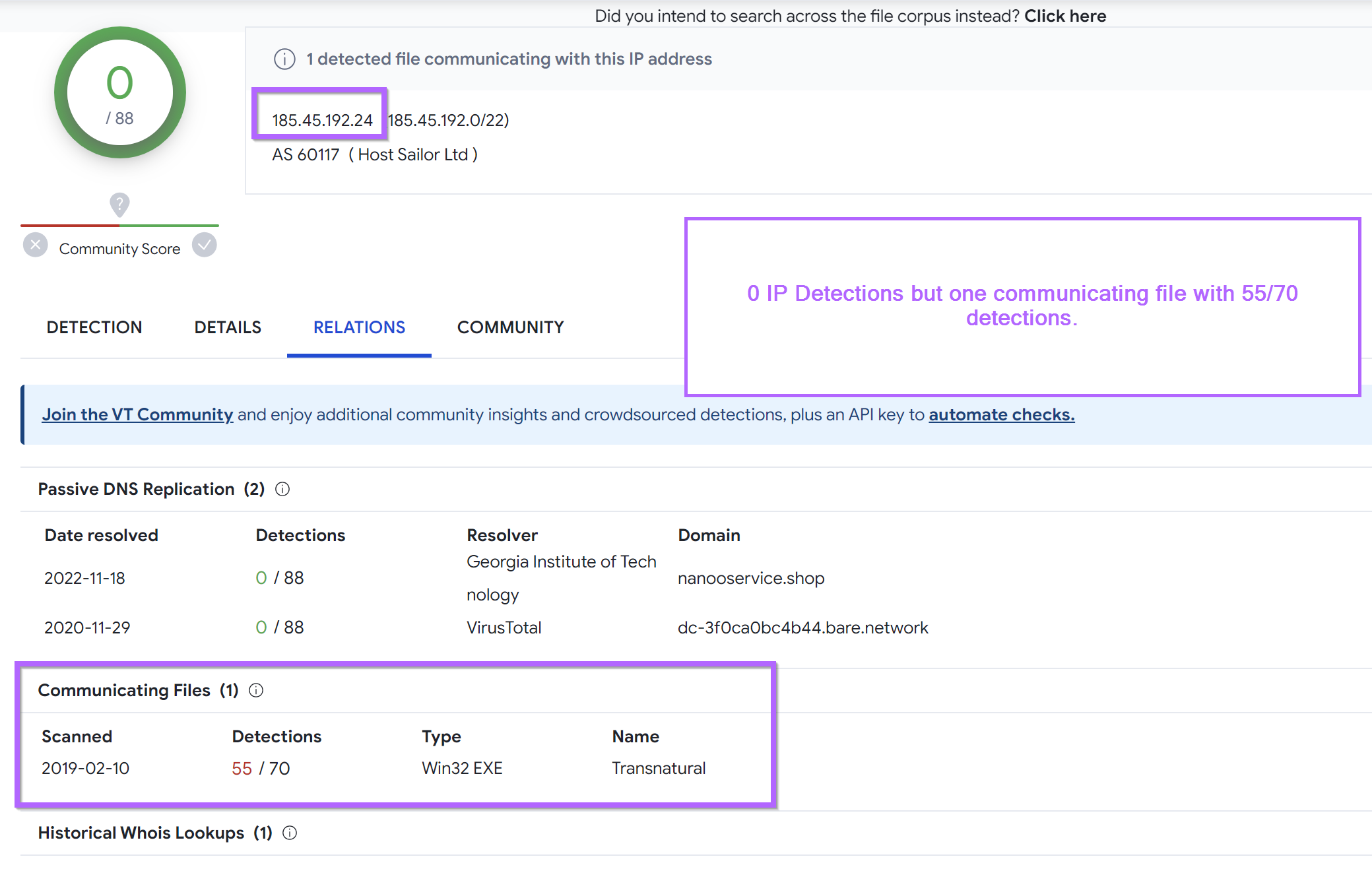
Looking at the first result 185.45.192[.]24, we can see 0 detections in Virustotal. But there is one communicating file with 55/70 detections.
Given the scan date of 2019-02-10, it's possible that the IP was previously malicious and that is no longer the case. But either way the IP is related to something shady.
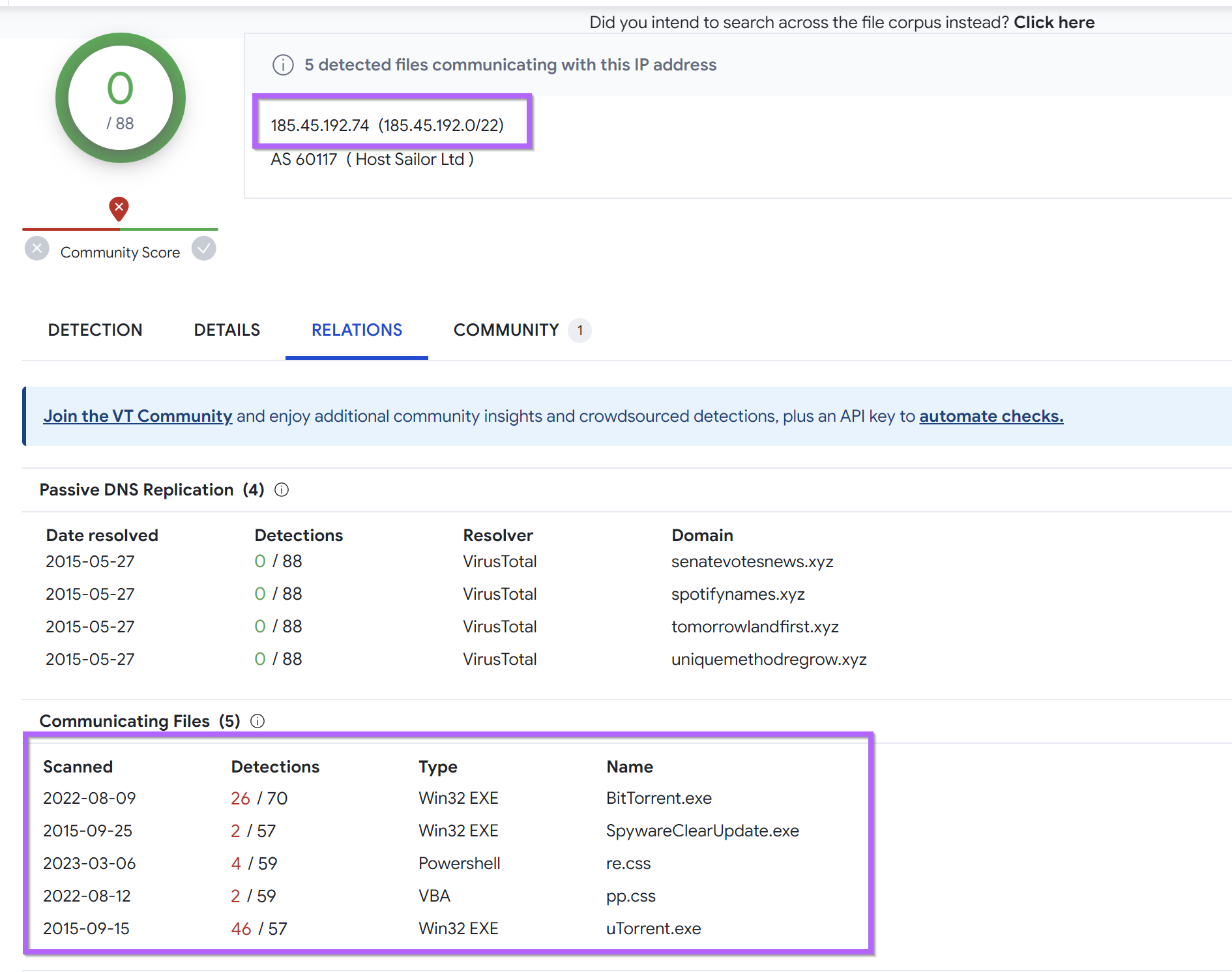
Checking on the second result of 185.45.192[.]74, we can also observe 0 IP detections, but 5 malicious communicating files.
Moving on, we can continue the same process and use it to determine more information.
Now there isn't enough information to strongly correlate the servers back to PrivateLoader, but given the very similar setups and small number of results. We can assume they are suspicious.
In cases like these, typically the servers are related and used by the same group, but not yet actively used for malicious activities. Some servers are often reserved for later use or the usage is (so far) so minimal that it hasn't yet showed up on VT and other "Free" services.
It's also entirely possible that some of these are benign, but I think the likelihood is low. All results should be considered suspicious and blocked where possible.
185.45.192[.]24 - 0/88 Detections, 1 communicating with with 55 detections.
185.45.192[.]74 - 0/88 VT, 5 malicious communicating files.
185.45.192[.]107 - 0/88 VT, no related files.
185.45.192[.]112 - 0/88 VT, no related files.
185.45.193[.]182 - 0/88 VT, no related files.
185.82.200[.]15 - 0/88 VT, no related files.
185.82.200[.]93 - 0/88 VT, no related files.
185.82.202[.]126 - 5/88 VT, Observed SSH Brute Forcing
185.117.75[.]107 - 0/88 VT, no related files.
185.183.96[.]10 - 4/88 VT, Hosting Malware, Previously Trickbot
185.198.57[.]70 - 12/88 VT, Previously Hosting Malware
185.198.57[.]117 - 9/88 VT, Initial PrivateLoader IP