Full Name
Matthew
Location
Melbourne, Australia
Matthew's Work
42 Posts

Manual identification, decryption and fixing of encrypted strings using Ghidra and x32dbg.

Manually Reversing a decryption function using Ghidra, ChatGPT and CyberChef.
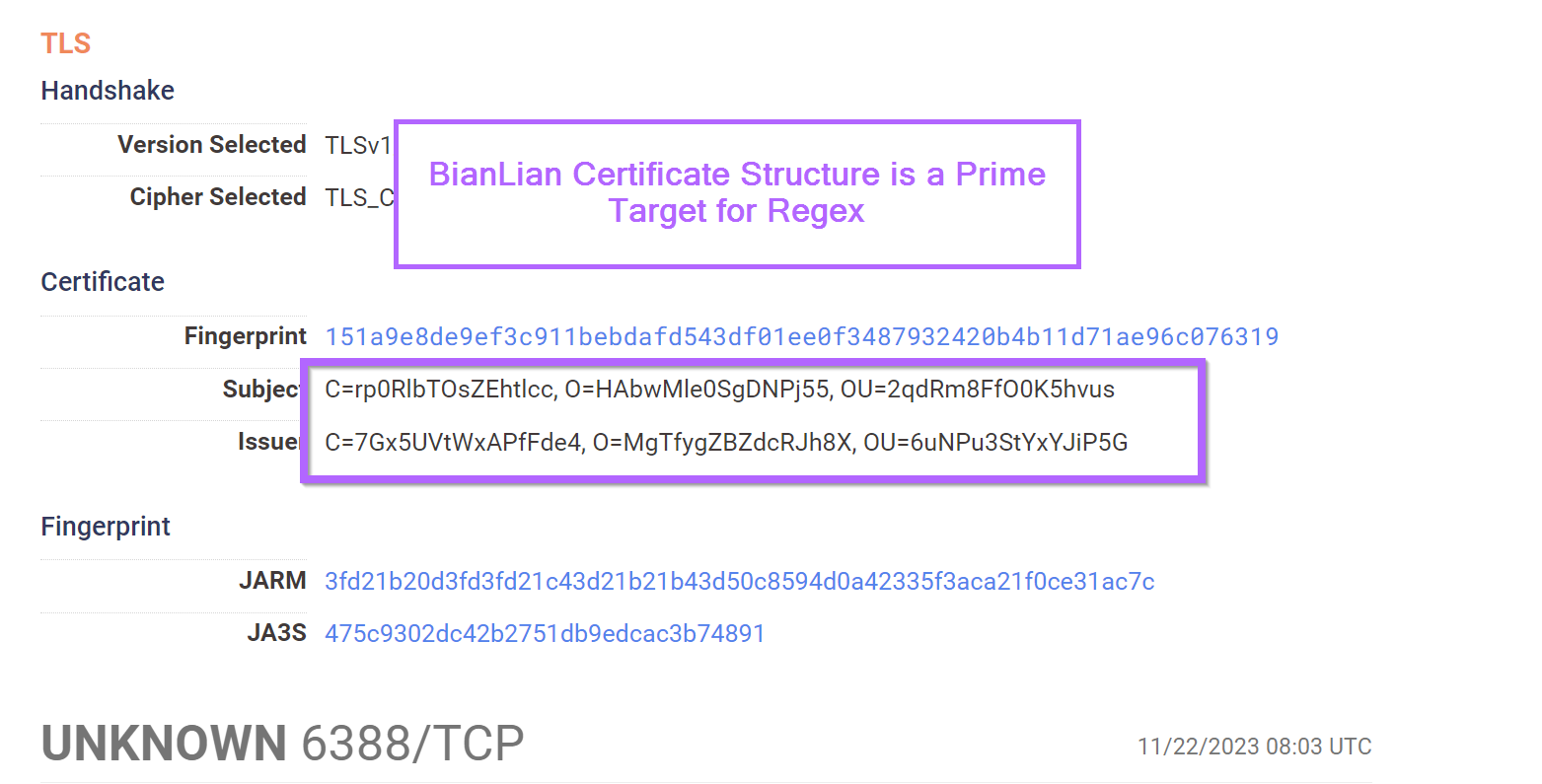
More interesting and practical queries for identifying malware infrastructure.
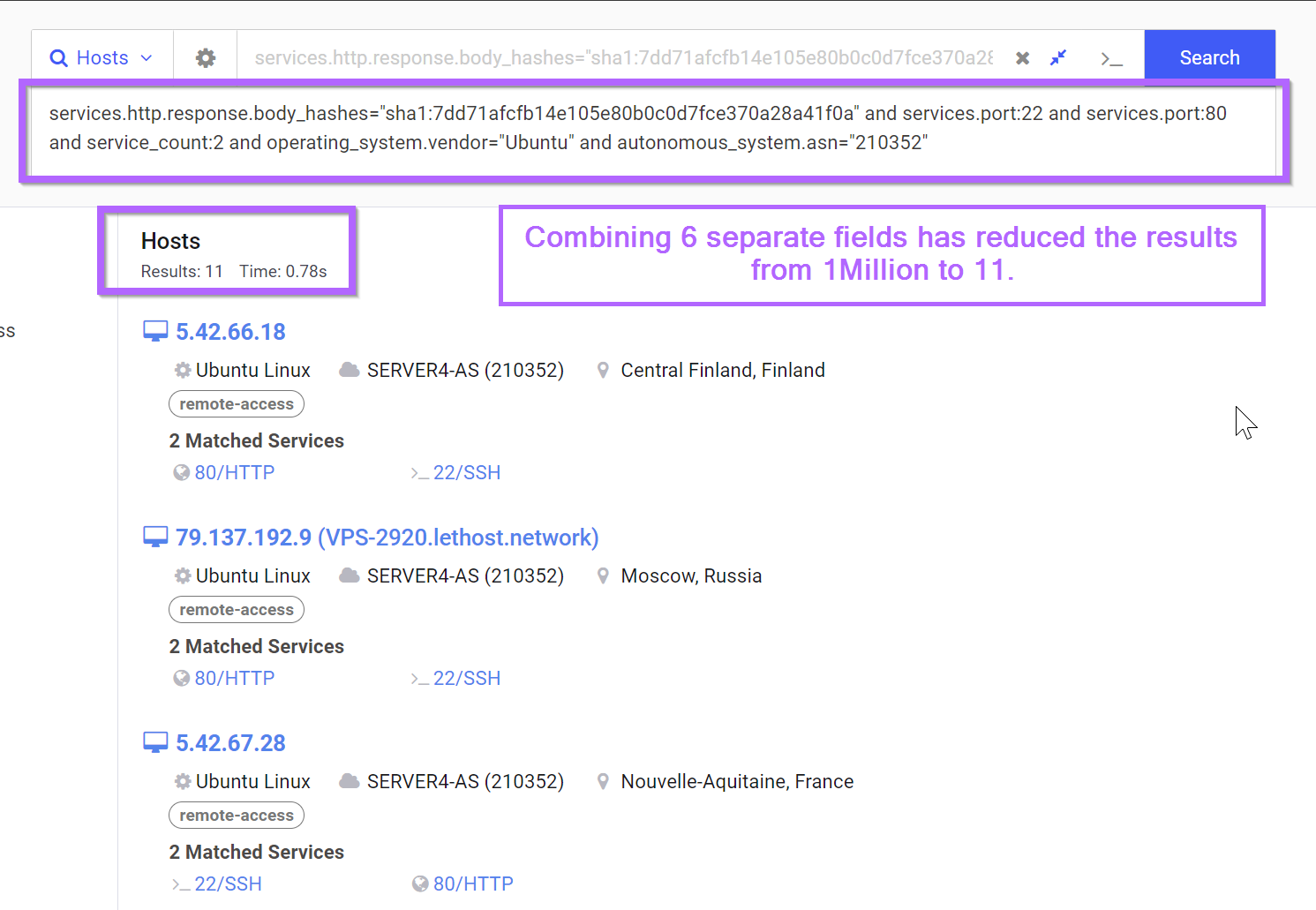
Identifying Malware infrastructure by combining weak pivot points.