How To Use Censys

Threat Intelligence Guides
|
Nov 30, 2023

Threat Intelligence Guides
|
Nov 27, 2023
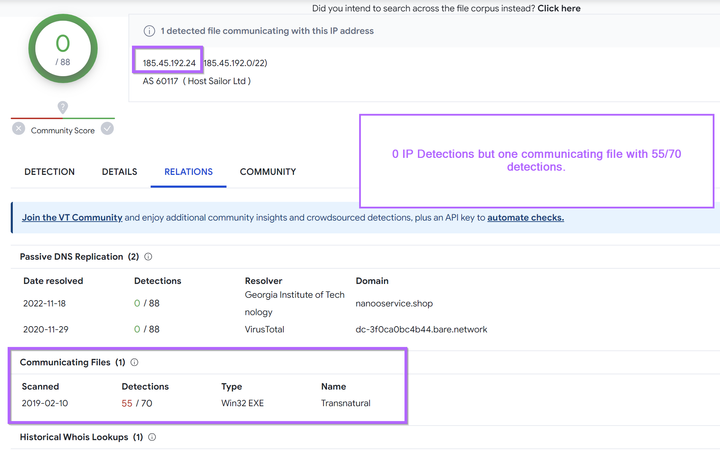
Threat Intelligence Guides
|
Nov 26, 2023

Threat Intelligence Guides
|
Nov 22, 2023
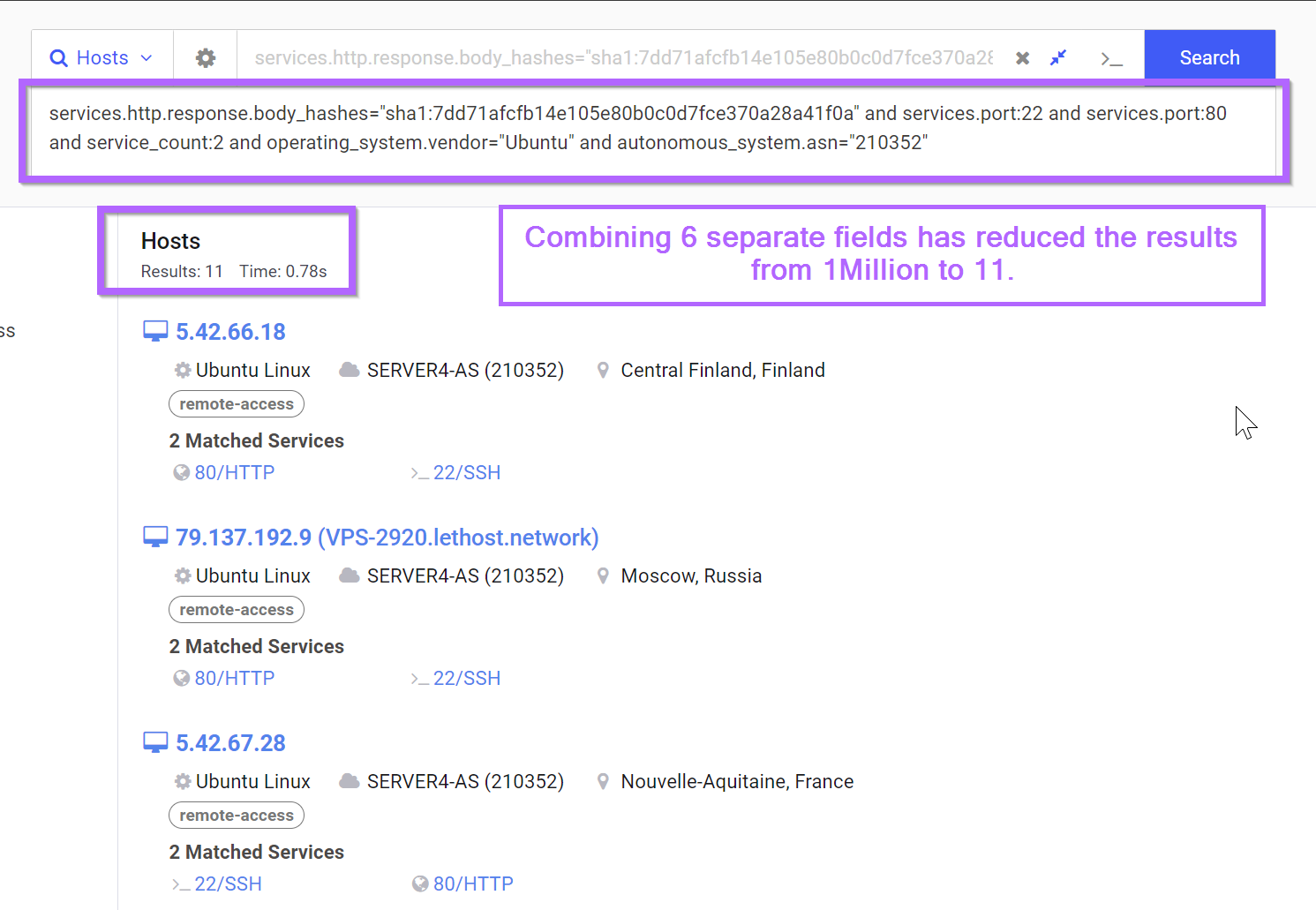
Threat Intelligence Guides
|
Nov 19, 2023
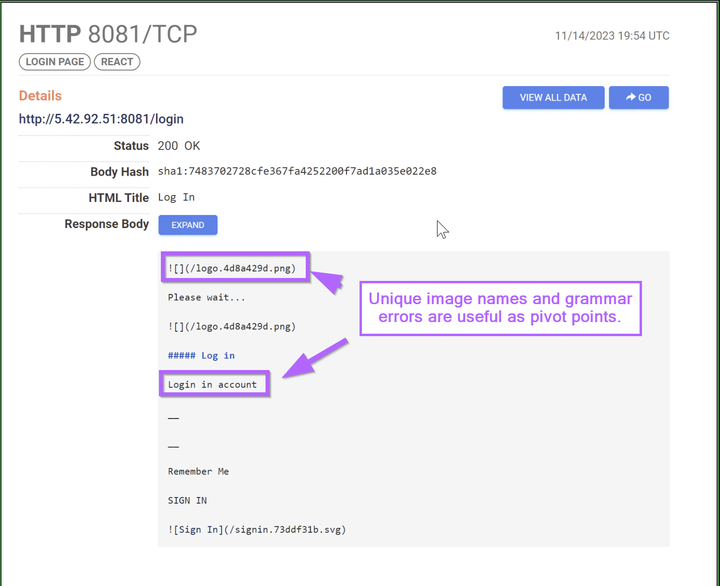
Threat Intelligence Guides
|
Nov 15, 2023
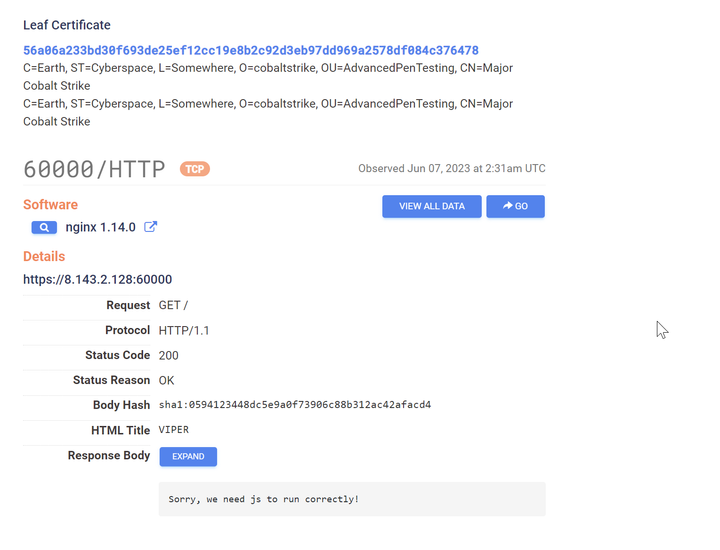
Threat Intelligence Guides
|
Oct 04, 2023

Threat Intelligence Guides
|
Jun 07, 2023
